
TOP SECRET//SI//REL USA, FVEY
Department of Government Efficiency
Information Paper 0x4E657720576F726C64204F72646572
AlligatorCon Europe 2025 Edition
11-13 September @ Kraków, Poland aka Pierogiland
-= [ AlligatorCon Europe 2025 ] =-
[--- We are currently clean on OPSEC.
My fellow Alligators! We have some very, very good news and a lot of good things are happening! AlligatorCon Europe will be back in 2025, and this year will be forever remembered as the year hacking was reborn, the year our packets destiny was reclaimed and the year that we began to make computers work again. For years, our species has been looted, pillaged and lied to by our enemies near and far. Hackers, crackers, phreaks, and skilled tinkerers really suffered greatly. We've been deprived of private exploits for months, but it is not going to happen anymore. Talks and workshops will come roaring back to our sacred venues. We will pry open firewalls and break down sanitizer routines. And ultimately we will go out for drinks and BBQ.
 We have yet so much to learn!
We have yet so much to learn!
[--- Rules of the Alligator
- You do not talk about AlligatorCon.
- You do not talk about AlligatorCon.
- If this is your first night at AlligatorCon, you have to hack.
- You can present using your IRC nick, Mastodon handle, BDSM dungeon moniker, whatever the hell you want but never with your real name.
- No cameras unless explicitly allowed by everyone in the picture, and no videos of the talks. If the spooks want to spy on us let's make them work for it.
- The contents or even the title of some talks may not be public, on request of the speaker. Never discuss them after AlligatorCon ends, or you'll be banned forever. And we mean it.
[--- Call For Participation
Send your proposal to: cfp@alligatorcon.eu  TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
 TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:- 2024 - Kraków... Kraków never changes
- 2023 - All Hail Our AI Overlords
- 2022 - We Survided The Pandemic And All We Got Was This Poster
- 2021 - 404 Conference Not Found
- 2020 - 404 Conference Not Found
- 2019 - Hell Yeah, AlligatorCon!
- 2018 - Keep Calm And AlligatorCon
- 2017 - Do Not Talk About AlligatorCon
- 2016 - The Horror! The Monstrosity! The Lulz!
- 2015 - The Alligator Goes International
[--- I am Jack's list of talks
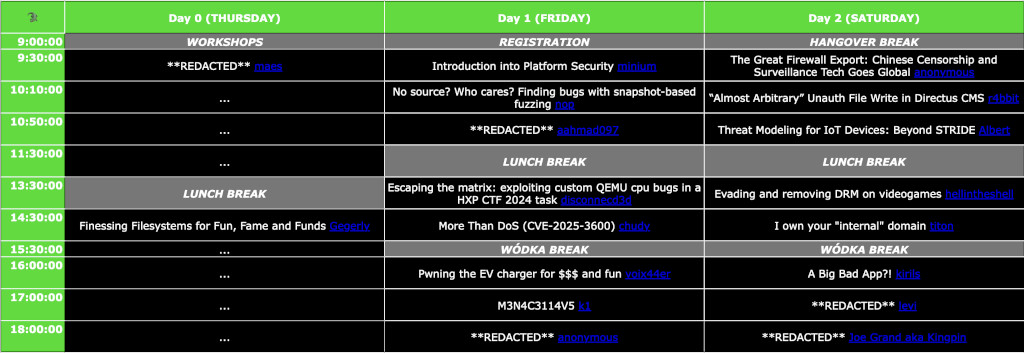
Title: [REDACTED]
Speaker: maes
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: Finessing Filesystems for Fun, Fame and Funds
Speaker: Gergely
I'm bringing exercises, material, anecdotes, exploits and bug bounty experience in a choose-your-adventure style training. Due to the limited time we have we'll have to find out what You'd like to do.
I have only one caveat to this:
I want everyone to learn a lot during the session.
What I come prepared with:
- a brain full of esoteric knowledge on the subject
- a laptop/github with some filesystem challenges
- all my past exploits (not current 0days though)
- bug bounty stories and experience
Even though I do macOS stuff mostly, a lot of the file-API/filesystem bugs translate well to other UNIX-like operating systems (and to a lesser extent to Windows).
We can sweat on the CTF, you can listen to me drone on for 4 hours or we can look for easy 0days for shits and giggles. It's up to you, as long as it's educational and/or really fun.
If we don't have time for something niche you'd like discussed: I am around, so feel free to ask away either at the conference or after.
Bring yourself, a laptop (if you want) and a optionally what you'd like to see out of this.
[---
Title: Introduction into Platform Security
Speaker: minium
This talk is a (hopefully) gentle introduction into the curious world of platform security. Among others, you'll learn how the UEFI boot process works, how different hardware components are involved and, most importantly, how things can go wrong.
[---
Title: No source? Who cares? Finding bugs with snapshot-based fuzzing
Speaker: nop
Reverse engineering, harnessing, and fuzzing in general can be a tedious and time intensive process - so why not add another layer?
Utilizing VM snapshots for fuzzing allows more granular control over what code to execute and holds the potential to significantly reduce the campaign setup effort.
We'll take a look at this concept, how to set up such a fuzzer for Windows targets, and check out what other advantages this technology offers.
[---
Title: [REDACTED]
Speaker: aahmad097
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: Escaping the matrix: exploiting custom QEMU cpu bugs in a HXP CTF 2024 task []
Speaker: disconnecd3d
In this talk we will go through the hxp_silicon_foundaries_hack4 challenge from HXP CTF 2024 where we had to break from a Linux VM and unprivileged shell that was running under QEMU emulation of a custom CPU. We will introduce the modified CPU from the challenge, which introduced a "scratch memory space" and custom SIMD-like instructions. We will exploit subtle bugs in the implementation to first escalate privileges and become root in the Linux VM and then to escape the QEMU and grab the flag from the host. We will do it all with the use of Pwndbg - a plugin for GDB & LLDB maintained by Disconnect3d.
[---
Title: More Than DoS (CVE-2025-3600)
Speaker: chudy
CVE-2025-3600 is an Unsafe Reflection vulnerability in the extremely popular and widely exposed Telerik Web UI. The default impact for this vulnerability is a Denial of Service. Basically, it allows you to DoS any application that uses this library and exposes the Telerik.Web.UI.WebResource.axd endpoint. Sounds fun, right? What if I tell you, that the impact may be higher, depending on the targeted codebase? If there's a product using Telerik Web UI, there's a chance that you may abuse the CVE-2025-3600 to find fun exploitation gadgets within the product codebase and achieve a higher impact, like RCE.
In this talk, I'll guide you through the CVE-2025-3600 and I'll show you how to look for custom RCE gadgets in the codebases that are using Telerik Web UI. I'll show you an example of the RCE gadget, which exists in the popular "enterprise grade" CMS solution.
[---
Title: Pwning the EV charger for $$$ and fun
Speaker: voix44er
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: M3N4C3114V5
Speaker: k1
$ nc -l -p 1906 -v
Listening on 0.0.0.0 1906
Connection from _ received!
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
[---
Title: [REDACTED]
Speaker: anonymous
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: The Great Firewall Export: Chinese Censorship and Surveillance Tech Goes Global
Speaker: anonymous
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: “Almost Arbitrary” Unauth File Write in Directus CMS
Speaker: r4bbit
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: Threat Modeling for IoT Devices: Beyond STRIDE
Speaker: Albert
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: Evading and removing DRM on videogames
Speaker: hellintheshell
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: I own your "internal" domain
Speaker: titon
Last year, I dug into the mess that is internal domain name collisions and found some wild stuff. Turns out, a ton of organizations—including major cities, police departments, an international airport, and Fortune 500 companies—are still leaking internal traffic to the internet without realizing it.
How? Because they're using old internal domains that never used to exist publicly, but now, thanks to ICANN's TLD expansion, do. So, naturally, I scooped up some interesting ones, like local.ad, internal.ad and wpad.ad, and watched as thousands of corporate laptops and workstations tried to connect, happily handing over credentials and internal requests in real-time.
I tried reporting it. Nobody cared. So, here we are. This talk is about the research, the impact, the domains I acquired, and what happens when internal traffic spills onto the open Internet. We'll also look at typo'ed nameservers (like akam.ne instead of akam.net), which let me intercept traffic from banks and multinational corporations.
We'll wrap up with why fixing this is a nightmare (hint: renaming an Active Directory domain is basically impossible), why disclosure sucks, and why this problem isn't going away anytime soon. If you know what WPAD, NTLM auth, or a DNS suffix is, you'll get a kick out of this.
[---
Title: A Big Bad App?!
Speaker: kirils
It's about shitty apps&corpos taking over our democracies. Societal hacking.
[---
Title: [REDACTED]
Speaker: levi
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: [REDACTED]
Speaker: Joe Grand aka Kingpin
[Not for public knowledge - you'll have to come here and find out!]
[---
Title: Lightning Talks
Speaker: .*
Country of origin: .*
The end of the last slot will be used for lightning talks. Just get up on stage and talk about whatever you want. Worst that can happen we throw pierogi at you.
[--- Life insurance pays off triple if you die on a conference trip
Free accomodation for this year is provided by Nvidia: their globally deployed ocean boilers finally made Central-European temperatures to raise enough so we all can just sleep on the nearest park bench in September.
 Heat the World!
Heat the World!
[--- We are the all singing, all dancing crap of the infosec world
The venerable Organizing Committee for this year will be:
- Kurwa Małpka, Count Crapula & The Face Dancer, the true Illuminati
- El Santa on original artwork
- Typhoid Mary on food and catering
- Billy McFarland on venue and accomodation Special thanks go to Xava Kosmosach for that original web design we keep rehashing every year since 2016. If anyone sees him and he asks why we haven't paid him for it yet, tell him... uhm... the check is on the mail or something, dunno.
[--- Sponsors
This year's event is proudly sponsored by 23andMe who will provide personalized horoscopes every time you flush.
 Special thanks to the law enforcement agencies from many countries for their relentless interest in our activities. We love you guys! #BlueLivesMatter
Special thanks to the law enforcement agencies from many countries for their relentless interest in our activities. We love you guys! #BlueLivesMatter

0x4E657720576F726C64204F72646572
[EOF]