
TOP SECRET//SI//REL USA, FVEY
National Security Agency/Central Security Service
Information Paper 0x4849205448455245
Alligator Europe Security Conference 2018
31 August & 1 September @ Areszt śledczy - Kraków, Poland aka PiSland



-= [ AlligatorCon Europe 2018] =-
The Alligators roam the streets of Kraków again!
Just like every year, we changed the venue and date. Why? Because why the hell not. At least you know you'll never be bored with us.
Some things never change though. Entry is and always will be 100% free. It's invite only, but hacking the registration web page still counts as a valid way to get an invite. We do not have sponsors or any sponsored content during the talks. The venue address and the location of all parties will be revealed at the last possible moment only to those who were invited, and you should not reveal it to anyone else.
We do welcome donations to keep the party going. All currencies are accepted, fiat or virtual. 0days and leaked documents are welcome as well, if you drop us any they will be shared on the torrents just for the lulz.
As a last minute surprise, we are also having a workshop on Thursday, one day before the event. It's a FIFO queue (first come, first serve) so if you want to attend make sure to send us an email ASAP.
There will also be free posters for everyone, designed by HackerStrip:
[--- Rules of the Alligator
- You do not talk about Alligator.
- You do not talk about Alligator.
- If this is your first night at Alligator, you have to hack.
- You can present using your IRC nick, Twitter handle, whatever the hell you want but never with your real name. Remember what Joey said, you don't have an identity until you have a handle.
- No cameras unless explicitly allowed by everyone in the picture, and no videos of the talks. There's no need to make it easy for the spooks.
- The contents or even the title of some talks may not be public, on request of the speaker. Never discuss them after Alligator ends, or you'll be banned forever. And we mean it.
Remember, kids: what happens in Kraków, stays in Kraków!
[--- Call For Participation
Send your proposal to: cfp@alligatorcon.eu  TL;DR just hack some shit and tell us how we can all do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The evaluation committee of AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, toppling dictatorships and bringing about the Revolution, all is good. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before: 2017 - 2016 - 2015
WHAT WE DON'T WANT: If you were thinking of telling us all about your new company product that scans for cyberthreats in the cloud using the blockchain on the Dark Web... don't waste such a wonderful talk on us! Go straight to John McAffee, he'll give you some excellent business and life advice.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
TL;DR just hack some shit and tell us how we can all do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The evaluation committee of AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, toppling dictatorships and bringing about the Revolution, all is good. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before: 2017 - 2016 - 2015
WHAT WE DON'T WANT: If you were thinking of telling us all about your new company product that scans for cyberthreats in the cloud using the blockchain on the Dark Web... don't waste such a wonderful talk on us! Go straight to John McAffee, he'll give you some excellent business and life advice.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
 TL;DR just hack some shit and tell us how we can all do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The evaluation committee of AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, toppling dictatorships and bringing about the Revolution, all is good. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before: 2017 - 2016 - 2015
WHAT WE DON'T WANT: If you were thinking of telling us all about your new company product that scans for cyberthreats in the cloud using the blockchain on the Dark Web... don't waste such a wonderful talk on us! Go straight to John McAffee, he'll give you some excellent business and life advice.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
TL;DR just hack some shit and tell us how we can all do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The evaluation committee of AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, toppling dictatorships and bringing about the Revolution, all is good. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before: 2017 - 2016 - 2015
WHAT WE DON'T WANT: If you were thinking of telling us all about your new company product that scans for cyberthreats in the cloud using the blockchain on the Dark Web... don't waste such a wonderful talk on us! Go straight to John McAffee, he'll give you some excellent business and life advice.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
[--- I am Jack's list of talks
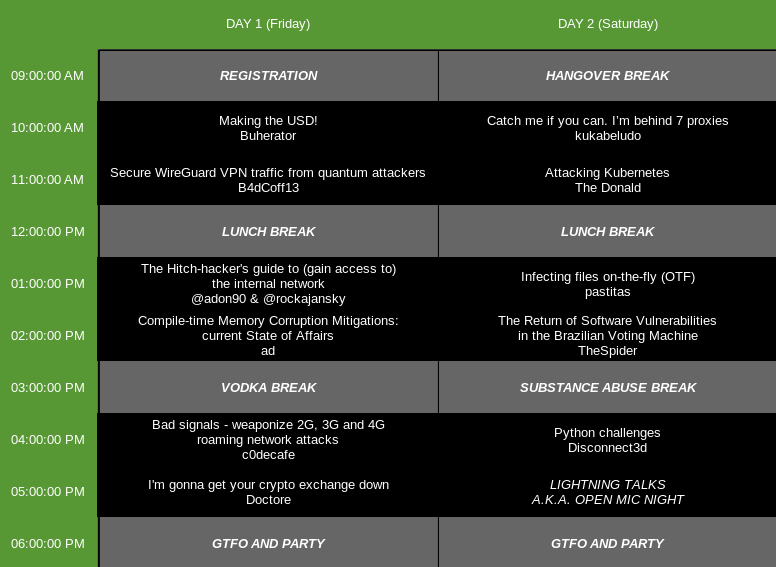 Hours of MS Paint went into this image.
Hours of MS Paint went into this image.
Title: Lightning Talks
Speaker: .*
Country of origin: .*
A slot will be reserved for lightning talks. Just get up on stage and talk about whatever you want. Worst that can happen we throw pierogi at you.
[---
Title: Infecting files on-the-fly (OTF)
Speaker: Pastitas
Country of origin: 🇪🇸 Fariñaland
Infecting files during a MITM attack is a common way of malware infection vector. Exists several tools to do it, free tools, commercial tools even leaked tools. Several drawbacks exists with this tools like Not real on the fly infection, only PE files infection.
I will present some techniques to avoid that drawbacks. The talk will not only be PE centric, I will talk about OTF infection of other file types. The topics covered are state of art, reverse engineer file types, ways to infect and protocol abusing. I will also use a Open Source tool I developed for these tasks.
[---
Title: The Return of Software Vulnerabilities in the Brazilian Voting Machine
Speaker: TheSpider
Country of origin: 🇧🇷 Huehueland
This presentation shows a detailed and up-to-date security analysis of the voting software used in Brazilian elections. It is based on results obtained by the authors in a recent hacking challenge organized by the Superior Electoral Court (SEC), the national electoral authority. During the event, multiple serious vulnerabilities were detected in the voting software, which when combined compromised the main security properties of the equipment, namely ballot secrecy and software integrity. The insecure storage of cryptographic keys, hard-coded directly in source code and shared among all 500,000 machines, allowed full content inspection of the software installation memory cards, after which two shared libraries missing authentication signatures were detected. Injecting code in those libraries opened the possibility of executing arbitrary code in the equipment, violating the integrity of the running software. We trace the history of the vulnerabilities to a previous security analysis, providing some perspective about how the system evolved in the past 5 years.
[---
Title: Attacking Kubernetes
Speaker: "The Donald" @ White House
Country of origin: 🇺🇸 Mordor
This talks' focus lays on a popular containerization tool called Kubernetes. Common implementations of Kubernetes are not secure by default and a lot of information about hardening is not known to the public. Since version 1.7 the security level has increased and common security misconfigurations have been mitigated. During this talk it will be demonstrated what happens if these mitigations are not applied and how to abuse them. The talk will be about both securing and attacking the platform and could be considered a 'purple team' talk. Multiple live demos are planned, most of them ending in a guest-to-host escape and a root shell.
[---
Title: I'm gonna get your crypto exchange down
Speaker: Doctore
Country of origin: 🇵🇱 PiSland
Crypto takes over the world. So many coins (mostly shitcoins but who cares?), so many exchanges and wallets online. As someone said “You can either rob a conventional bank or a crypto currency company. Both have millions, but unlike traditional banks, cryptocurrency companies are startups with only 20 people.” Hundreds of billions of dollars are lying on the street to pick them up. And you on the other side who wants to rule them all!
This talk will show you how to start with easy pentest of cloud crypto wallet dedicated for particular coin and end up with shutting down the crypto exchange with the GDPR in the background. No demo because it’s down :(
[---
Title: Catch me if you can. I’m behind 7 proxies.
Speaker: kukabeludo
Country of origin: 🇧🇷 Huehueland
Privacy is a dream far away to be a reality in our life. But how to reduce the impacts of surveillance? The adversaries’ ability to compromise TOR RELAYS is mining our trust in anonymous networks such as TOR but this war is not totally lost. How to defeat the TOR compromised relays?
The ability of read all your text messages including but not limited to emails, SMS messages, Telegram, Whatsapp, Signal conversations and let’s not forget about all your phone calls, gives the adversary total control over your communication channels. What about the alternatives?
Giving a special attention to the problems related with the TOR network. This presentation will analyze some de-anonymization techniques which allowed surveillance agencies to identify TOR users. I will propose an approach to invalidate those techniques. The idea is to reduce and difficult powerful attacks such data correlation attacks, even considering that your adversary has a full compromised TOR RELAYs and your sensitive data is prone to pass by those compromised relays.
As a bonus I will present a tool which solves the principal TOR NETWORK issues like:
- Stability: TOR is considered an unstable network. The packet loss is high and seems that it’s an eternal problem for such kind of anonymous network. How to solve this issue?
- Speed: The anonymity behind the TOR network is based on the capability of this network in make your connection hop a couple of times before reach the final destination. Those hops can happen in countries from different continents and this slow down the speed of TOR NETWORK. My solution allows you to watch movies in High Resolution in YOUTUBE, and use TOR network for everything without fell the pain of use a considered “slow network”.
- Compromised Relays: The number of TOR compromised relays is increasing. The adversary can intercept your data even inside the anonymous network. This tools reduces the chances of a successful data correlation.
[--- I am Jack's list of workshops
Title: BLE security workshop
Speaker: smartlockpicking
Country of origin: 🇵🇱 PiSland
In this workshop you will get familiar with the basics of BLE security. We will work on a dedicated, readily available BLE hardware nRF devkit device. In a minutes you will turn into embedded developer and learn how to program your own BLE device yourself, using a free web interface and ready templates. Next, from attacker's perspective, we will cover among others: sniffing, spoofing, MITM, replay and relay. Having enough time, we will play with a collection of vulneraBLE smart locks, sex toys and other devices. The takeaway hardware included will allow you to experiment and repeat the exercises later at home.
The hardware pack includes:
- nRF BLE devkit that can be flashed as a BLE RF sniffer, or a BLE device to attack
- ST-Link debugger for flashing the devkit firmware
- 2xBLE USB dongles
- contemporary laptop that can run Kali Linux in VM (like 4 GB RAM, 20G disk space), with VM software of your choice installed (virtualbox or vmware), and at least 2 USB ports available
- smartphone with BLE support, preferably Android (at least 4.3), or iPhone (at least 4s)
- if you have Raspberry Pi 3, you can bring it too
- you can also bring your own BLE devices
[--- Life insurance pays off triple if you die on a conference trip
The recommended place for your stay in Kraków is the 5 star hotel Areszt Śledczy Kraków-Podgórze. Just knock on the door, tell them all about your hacking feats, and you'll find nice people who will be more than happy to let you in - for free! With some luck you can even score a presidential suite if you are bald and dressed in sportswear.
Alternatively, here are a few -possibly more comfortable- venues you can try out:
If you're on a budget, Greg & Tom hostel at Ul. Florianska is quite decent, centrally-located and has a nice bar too. Additionally, this city has a really amazing CouchSurfing community that you should definitely reach out to. You're also welcome to bring a sleeping bag and crash on a friendly local hacker's home, a popular choice of Alligator attendees every year.
Transport arrangements are prepared for the occasion in the form of a rusty van with the words FREE CANDY spray painted on the side and the picture of a funny bear you may have seen on 4chan before. Trust the nice man with the moustache, he'll take you where you want to go.
 Seems legit.
Seems legit.
[--- We are the all singing, all dancing crap of the infosec world
The venerable Organizing Committee for this year will be:
- Kurwa Małpka & Count Crapula, the original chaos monkeys
- Xava Kosmosach on web design
- Santaplix @ Hackerstrip on original artwork
- Toxic Avenger as our BOFH
- Donald Trump on motivational speeches
- Shia LaBeuf as our personal life coach
- ...and always with us, Our Lord Satan whom we praise
[--- Sponsors
This event is proudly sponsored by: Soplica Vodka, Paper Street Soap Company, The George Soros Foundation, Russian Ministry of Fake News and Propaganda, Lifetime President of China Xi Jinping, His Majesty King T'Challa of Wakanda, and many others who prefer to remain anonymous but the NSA already knows who you are. No, seriously. They know everything. Run. Run for your lives.
This year we will be missing the iconic old dude of Kazimierz, Mikołaj. May you roam the bars of Infinity now, old pal.



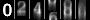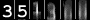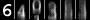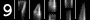
0x4849205448455245
[EOF]
