
TOP SECRET//SI//REL USA, FVEY
National Security Agency/Central Security Service
Information Paper 0x4255444150455354
AlligatorCon Europe 2019 Edition
16 & 17 August @ Büntetés-végrehajtás Országos Parancsnoksága - Budapest, Hungary aka Goulashland



-= [ AlligatorCon Europe 2019 ] =-
The Alligators roam Europe once again! Keeping the tradition of holding this conference in authoritarian countries, this time we are gathering at the beautiful city of Budapest, where its unsuspecting citizens have no idea what horrors await them...
 TFW we realized we have no idea either
TFW we realized we have no idea either
 You'll be the coolest kid in the block with this poster in your bedroom!
You'll be the coolest kid in the block with this poster in your bedroom!
[--- Rules of the Alligator
- You do not talk about AlligatorCon.
- You do not talk about AlligatorCon.
- If this is your first night at AlligatorCon, you have to hack.
- You can present using your IRC nick, Mastodon handle, BDSM dungeon moniker, whatever the hell you want but never with your real name.
- No cameras unless explicitly allowed by everyone in the picture, and no videos of the talks. If the spooks want to spy on us let's make them work for it.
- The contents or even the title of some talks may not be public, on request of the speaker. Never discuss them after AlligatorCon ends, or you'll be banned forever. And we mean it.
[--- Call For Participation
Send your proposal to: cfp@alligatorcon.eu  TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The Honorable Evaluation Commitee AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
WHAT WE DON'T WANT: We all know how fun it is to make your employer pay for your party trip, but there is a strict rule of NO CORPORATE BS TALKS. Nobody gives a flying crap who your employer is and how the product you're selling will change our lives and how many multi-letter certifications you got - just hack stuff or shut up.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The Honorable Evaluation Commitee AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
WHAT WE DON'T WANT: We all know how fun it is to make your employer pay for your party trip, but there is a strict rule of NO CORPORATE BS TALKS. Nobody gives a flying crap who your employer is and how the product you're selling will change our lives and how many multi-letter certifications you got - just hack stuff or shut up.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
 TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The Honorable Evaluation Commitee AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
WHAT WE DON'T WANT: We all know how fun it is to make your employer pay for your party trip, but there is a strict rule of NO CORPORATE BS TALKS. Nobody gives a flying crap who your employer is and how the product you're selling will change our lives and how many multi-letter certifications you got - just hack stuff or shut up.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The Honorable Evaluation Commitee AlligatorCon is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
WHAT WE DON'T WANT: We all know how fun it is to make your employer pay for your party trip, but there is a strict rule of NO CORPORATE BS TALKS. Nobody gives a flying crap who your employer is and how the product you're selling will change our lives and how many multi-letter certifications you got - just hack stuff or shut up.
HOW WE WANT IT: Our format is the following: one hour slots for everyone, but how much you use is completely optional. We recommend 40 minute talks, to give people time to drink a beer or mate, chat and relax before the next talk. For really quick topics (5-10 minutes) it's probably best to use the lightning talks slot, it's free-for-all -- just like a rap battle, you go up on stage and grab the mic.
[--- Life insurance pays off triple if you die on a conference trip
Free accomodation and transport arrangements this year will be available to all attendees, generously donated by the BvOP. It's always refreshing to see support for the infosec community!
 What could possibly go wrong?
What could possibly go wrong?
[--- I am Jack's list of talks
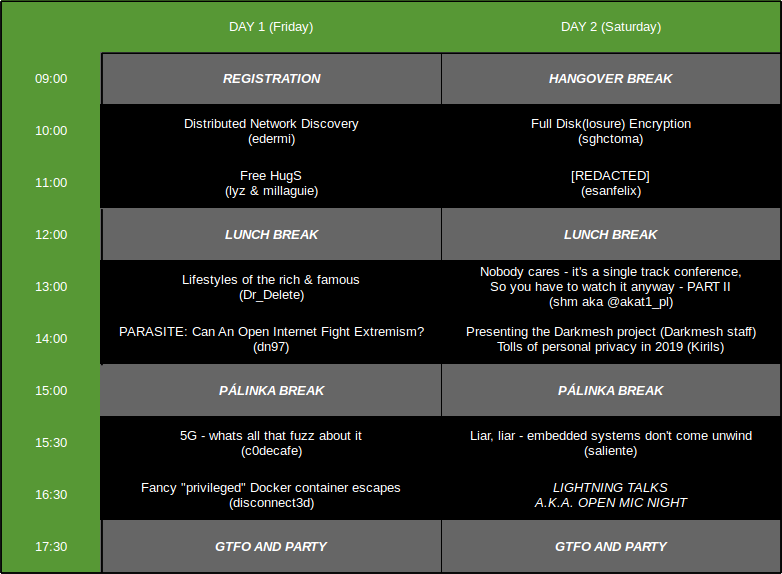 Hours of MS Paint went into this image.
Hours of MS Paint went into this image.
Title: Lightning Talks
Speaker: .*
Country of origin: .*
A slot will be reserved for lightning talks. Just get up on stage and talk about whatever you want. Worst that can happen we throw milkshakes at you.
[---
Title: Nobody cares - it's a single track conference, so you have to watch it anyway - PART II
Speaker: shm aka @akat1_pl
Country of origin: 🇵🇱 Poland aka Cebulandia
$ id
uid=65534(nobody) gid=65534(nobody) groups=65534(nobody)
$ ./a.out
# id uid=0(root) gid=0(wheel) (...)
[---
Title: 5G - whats all that fuzz about it
Speaker: c0decafe
Country of origin: 🇩🇪 Germany aka Beerland
During the talk I'll get rid of some of the fancy features everybody claims about 5G telekommunikation networks. I'll show whats really behind the next gen telko standart in the most brutal technical way possible.
[---
Title: Lifestyles of the rich & famous
Speaker: Dr_Delete
Country of origin: 🇧🇷 Brazil aka HueHuEland
Abstract redacted - you will have to come here to know what it is about.
[---
Title: PARASITE: Can An Open Internet Fight Extremism?
Speaker: dn97
Country of origin: 🇮🇪 Northern Ireland aka Little Alabama
It's no secret that people are more interconnected than ever: not only is it incredibly convenient to contact old friends and distant family, but thanks to the open internet we can engage with strangers all over the world at the press of a button. A single tweet can gain thousands of interactions from strangers seemingly at random: what could possibly go wrong?
In this talk, I touch on a wide variety of subjects related to the complex relationship between extremism & the internet: among these, I will be exploring the various stages of how extremism manifests itself online and the methods that they will employ to achieve their goal: whether that be recruitment, intimidation or simply to organise amongst themselves.
Can we combat this threat while still keeping the internet open? Is the burden too much for service providers like Google & Facebook alone? What is the role of governments, and how do we collaborate? What is censorship? When does it become negligence? And most importantly, will I have to talk about machine learning?
Expect a healthy mix of technical and soft content. No prior knowledge will be assumed, so strap in!
[---
Title: Presenting the Darkmesh project
Speaker: Darkmesh Staff
Country of origin: 🌍 The Internet
We are creating an open mesh (distributed vpn based on tinc) to anyone interested in sharing their projects with other people like them without putting it on internet, contact with others in a (not very) anonymous way or use it in the way they want.
We are targeting hackerspaces, makerspaces and other *spaces to use this network as way to share among them.
Yes! there are other initiatives like this, like dn42, and we are interconnecting with them, we provide access to this network, chaosnet and others but easier and less red tape.
We are also creating some services inside the mesh, like our own DNS system, PKI, IRC servers and more.
[---
Title: Free HUgS
Speaker: lyz & millaguie
Country of origin: 🇪🇸 Spain aka Expensive Portugal
In the *newly* born DevSecOps world, all the efforts are focused on the hardening of the development process. Nevertheless, we'll show that the toolbox can be used to automatically hunt vulnerabilities in open source projects as soon as there is a new release.
[---
Title: Liar, liar - embedded systems don't come unwind
Speaker: saliente
Country of origin: 🇫🇮 Finland aka North of the Wall
The connected society relies on speed and information availability. It relies on data, measurements, observations, analysis and notifications. Decision making is likely to be increasingly automated. The data is being provided by or produced with e.g. embedded systems. Data integrity and non-repudiation are important because this data is supporting decision making within the critical infrastructure and on top of it.
The talk is about detecting data manipulation attacks with graph convolutional networks.
[---
Title: [REDACTED]
Speaker: esanfelix
Country of origin: 🇪🇸 Spain aka Expensive Portugal
Abstract redacted - you will have to come here to know what it is about.
[---
Title: Distributed Network Discovery
Speaker: edermi
Country of origin: 🇩🇪 Germany aka Beerland
Finding services in a network is part of the daily business. Whereas there are free, platform independent scanners that have large protocol support or reach line speed, there are no solutions with builtin and automated work distribution capabilities.
In this talk, nray, a port scanner written from scratch, is going to be introduced. Apart from the ability to run in a distributed manner, it brings a lot of outstanding features that are going to ease the life of its users as well as some fresh ideas to the field of network discovery.
[---
Title: Full Disk(losure) Encryption
Speaker: sghctoma
Country of origin: 🇭🇺 The Mighty Dictatorship of Football Stadiums and Billionare Gas Fitters (aka Hungary)
I'm going to talk about a work in progress reverse engineering effort of a major FDE product. After a short introduction to the Windows Master and Volume Boot Records, I'll show what the target software's VBR do, and how it tries to hide a small partition full of information necessary for all the fancy features.
Besides reversing the VBR's 16-bit real mode code, it was also necessary to understand some proprietary file formats - including a custom database format. I will show how I got from using strings through simple Python scripts to a full-blown script that utilizes Kaitai Struct to dump the database. At the end, I will summarize what data can already be obtained from an ecrypted disk, and what tasks are still to be done.
[---
Title: Fancy "privileged" Docker container escapes
Speaker: disconnect3d
Country of origin: 🇵🇱 Poland aka Cebulandia
This talk will show different ways to escape privileged Docker containers. While people rather know not to use --privileged, you don't need to run a docker container with --privileged flag to make it insecure.
Many sources on the net mentions that, for example, the SYS_ADMIN capability makes your container insecure but it's hard to find explanations with PoCs. The talk will show and explain 2-3 methods based on SYS_ADMIN and maybe some other insecure options (disabling apparmor/seccomp or enabling additional cgroup access).
[---
Title: Toll of personal privacy in 2019
Speaker: Kirils
Country of origin: 🇱🇻 Latvia aka Over The Rainbow
Updated for 2019 for the first time, this talk revisits the theme of personal privacy in the digital world, shedding light upon the motivation behind caring about one's privacy. Author also talks about their personal privacy choices that they made in the past and how those affected their life, discussing the dawn of loyalty cards, biometric passports, banking services, CCTV, and certification programs.
[--- We are the all singing, all dancing crap of the infosec world
The venerable Organizing Committee for this year will be:
- Kurwa Małpka & Count Crapula, controlling everything from the shadows
- El Santa on original artwork
- Toxic Avenger as our BOFH
- Julian Assange on press releases
- Sabrina Spellman on magic and potions
- Pinky & The Brain on world domination
- ...and always with us, Our Lord Satan whom we praise
[--- Sponsors
This event is proudly sponsored by: Paper Street Soap Company, Bellingcat, Internet Research Agency (IRA), US Cyber Command, The Church of Satan, George Soros & Open Society Foundations, and the New World Order.
Special thanks to the law enforcement agencies from many countries for their relentless interest in our activities. We love you guys! #BlueLivesMatter

0x4255444150455354
[EOF]