
TOP SECRET//SI//REL USA, FVEY
National Security Agency/Central Security Service
Information Paper 0x74686520656E64206973206E696768
AlligatorCon Europe 2024 Edition
5, 6 and 7th of September @ Kraków, Poland aka Pierogiland

-= [ AlligatorCon Europe 2024 ] =-
[--- Kraków... Kraków never changes
This is it, folks! We are living in the future! Although... it's not exactly the future we were promised. Instead of a shiny Space Era where we boldly go where no one else has gone before, we are stuck on Earth. We do have self driving cars, but they can be fooled by a sticker. We've got AI but all we can ask them to do is set an alarm for tomorrow, change the song we're listening to, make incredibly shitty art or write even buggier code than we already write ourselves. So, let's head back to the past! Let's celebrate the dreams of a future that was still great!
 Never forget what they took from us
Never forget what they took from us
 You'll be the coolest kid in the post-apocalypse with this poster in your nuclear shelter!
You'll be the coolest kid in the post-apocalypse with this poster in your nuclear shelter!
[--- Rules of the Alligator
- You do not talk about AlligatorCon.
- You do not talk about AlligatorCon.
- If this is your first night at AlligatorCon, you have to hack.
- You can present using your IRC nick, Mastodon handle, BDSM dungeon moniker, whatever the hell you want but never with your real name.
- No cameras unless explicitly allowed by everyone in the picture, and no videos of the talks. If the spooks want to spy on us let's make them work for it.
- The contents or even the title of some talks may not be public, on request of the speaker. Never discuss them after AlligatorCon ends, or you'll be banned forever. And we mean it.
[--- Call For Participation
Send your proposal to: cfp@alligatorcon.eu  TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
 TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:
TL;DR just hack some shit and tell us how we all can do it too, for teh lulz.
Now for the long version...
WHAT WE WANT: The AlligatorCon Honorable Evaluation Commitee is interested in no-nonsense talks about hacking. We prefer technical talks but non-technical yet "unusual" ones are good too - the further you stray from your typical conference talk, the better. Bonus points for presentations that include code, practical examples, and live demos. The usual topics include pentesting, exploitation, pwnage, 0days, phreaking, rootkits, radio, satellites, spreading knowledge, evading censorship, old sch00l shit, new sch00l shit, worshipping Satan, raising the dead, fun times. Confidentiality is key, so don't hesitate to propose topics that "legit" conferences would never accept. You can check out the schedules for previous years to give you an idea of what's been presented before:- 2023 - All Hail Our AI Overlords
- 2022 - We Survided The Pandemic And All We Got Was This Poster
- 2021 - 404 Conference Not Found
- 2020 - 404 Conference Not Found
- 2019 - Hell Yeah, AlligatorCon!
- 2018 - Keep Calm And AlligatorCon
- 2017 - Do Not Talk About AlligatorCon
- 2016 - The Horror! The Monstrosity! The Lulz!
- 2015 - The Alligator Goes International
[--- I am Jack's list of talks
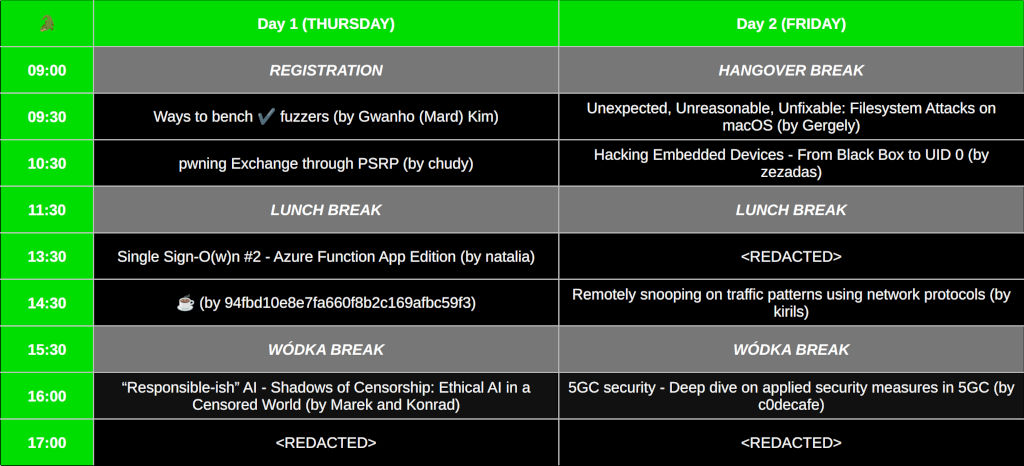
Title: Ways to bench ✔ fuzzers
Speaker: Gwanho (Mard) Kim
Country of origin: 🇰🇷 South Korea aka Kimchiland
This talk will demonstrate that, with your home-brewed fuzzer, you will be able to get better performance than the popular general fuzzers like AFL (American Fuzzy Lop). At the start, we will discuss the basics of fuzzing and architectures. After that, you will learn tricks that you would like to use to optimize for faster performance and to make your fuzzer "smarter" so that you can get more bugs for $$$. After that, we will talk about tips and tricks when it comes to trying to benchmark, like evaluating fuzzers using how many bugs you find in the vulnerable machine, or using a popular benchmark suite, FuzzBench. When we are nearing the end, we willevaluate the performance as a graph using the feedback logs you got from your fuzzer, and maybe, if we have time, we will also demonstrate this using my own home-made fuzzer called Strawberry Soju.
[---
Title: pwning Exchange through PSRP
Speaker: chudy
Country of origin: 🇵🇱 Poland aka Bimberland
Custom deserialization + PowerShell + Exchange == cool RCE chains
[---
Title: Single Sign-O(w)n #2 - Azure Function App Edition
Speaker: natalia
Country of origin: 🇵🇱 Poland aka Bimberland
Single Sign-On comes in all shapes and misconfigurations. This year, I would like to present a case study of an insecure Azure Function App instance. I will explain how an improperly configured SSO allowed me to gain unauthorized access to a critical functionality during a recent pentest. You will also discover when a globally unique Application ID URI is not unique after all and learn how to exploit this subtle detail to gain access to insecure Function Apps in other tenants. Let’s conquer the cloud together!
[---
Title: ☕
Speaker: 94fbd10e8e7fa660f8b2c169afbc59f3
Country of origin: 🇦🇹 Austria aka Schnitzelland
enjoy a technical talk about ☕ + 🖥️
[---
Title: “Responsible-ish” AI - Shadows of Censorship: Ethical AI in a Censored World
Speaker: Marek and Konrad
Country of origin: 🇵🇱 Poland aka Bimberland
In an era of rapid AI evolution, the emphasis on Responsible AI underscores the importance of ethical integrity, fairness, and transparency. Our work delves into the nuanced impact of censorship on AI, analyzing its effects on transparency, biases, and global deployment. We explore both historical and contemporary cases of censorship, assessing their influence on AI's reliability and the resultant societal implications, including aspects of surveillance, cybersecurity, and public discourse. Addressing the dual challenges of fostering innovation while upholding ethical standards, our discussion navigates the complex terrain of censorship's restrictive influence on AI's learning capabilities and innovation. We highlight the critical balance needed between freedom of information and the ethical dilemmas posed by data censorship. Moreover, we contemplate the future landscape of AI regulation and the potential for an uncensored AI future, advocating for the development of guidelines that promote ethical advancement without unnecessary constraints. Through this exploration, we aim to spark a conversation on the ethical dilemmas of balancing diversity with historical accuracy in AI-generated content, seeking to navigate these intricate issues for ethical AI development.
[---
Title: Unexpected, Unreasonable, Unfixable: Filesystem Attacks on macOS
Speaker: Gergely
Country of origin: 🇭🇺 Hungary aka Goulashland
This talk is about filesystems, 0days and bug bounties. I will discuss how I discovered vulnerabilities in macOS, how I (re)discovered some old and new techniques, and how I used this all to bootstrap my career as an independent security researcher. I started at not knowing anything about macOS, and I will show you how I got to the point where I could find 6 high-severity 0-days in it. I will expand on the previously presented material (at OBTS) by including my experiences in Apple's bug bounty program (it's a mixed bag), and by extending the primitives to be less macOS-specific.
If you are interested in any of the following, this talk is for you: logic bugs, filesystems, Apple, bug bounties.
To understand the talk, only a basic understanding of filesystems and POSIX file APIs is required.
[---
Title: Hacking Embedded Devices - From Black Box to UID 0
Speaker: zezadas
Country of origin: 🇵🇹 Portugal aka Cheap Spain
Join Zezadas on the journey "Hacking Embedded Devices - From Black Box to UID 0" where hacking embedded devices takes on a new dimension. This presentation covers the process of achieving root access on an embedded device with no prior information by combining exploits and reverse engineering techniques. Throughout this presentation, you will learn methods to identify hardware specifications, conducting decompilation and analysis of Android Applications and Linux binaries. This acquired knowledge will be applied to uncover and exploit vulnerabilities within embedded systems. Together, they'll showcase that hacking embedded devices isn't as intimidating as it may seem and that it can be an adventure worthy of a time-traveling DeLorean. Get ready to explore the boundaries of time as Zezadas exploit a device misconfiguration to gain root shell access. This unique approach showcases the ingenuity of hackers who can make the past and present converge in unexpected ways.
[---
Title: Remotely snooping on traffic patterns using network protocols
Speaker: kirils
Country of origin: 🇱🇻 Latvia aka Over The Rainbow
There was the ping of death, flood ping, all affecting the A of the CIA; and now we present - ping snooping to attack the C!
[---
Title: 5GC security - Deep dive on applied security measures in 5GC
Speaker: c0decafe
Country of origin: 🇩🇪 Germany aka Beerland
Last year I talked about the new security improvements in the 5G Core, this year we are going to get a deep dive into all the 5G SA standardized security features. How is the 5GC Management Bus secured? Why can i not do nasty things on the GRX anymore [or can I?] and what does all of this has to do with our beloved X509 certificates? As a bonus This talk will also cover some very useful additions to the infrastructure when it comes to the user's privacy needs.
[---
Title: Lightning Talks
Speaker: .*
Country of origin: .*
The end of the last slot will be used for lightning talks. Just get up on stage and talk about whatever you want. Worst that can happen we throw pierogi at you.
[--- Life insurance pays off triple if you die on a conference trip
Free accommodation is kindly provided by Elon Musk and his team of scientists, all you have to do is let them burrow inside your brain for a bit so they can put a chip in it, no biggie. Free hosting and 5G straight into your mind? That's a win-win, folks!
 Our most generous sponsor yet
Our most generous sponsor yet
[--- We are the all singing, all dancing crap of the infosec world
The venerable Organizing Committee for this year will be:
- Kurwa Małpka, Count Crapula & The Face Dancer, the true Illuminati
- El Santa on original artwork
- Elon Musk on human experimentation
- Javier Milei on accounting and animal cloning
- Vladimir Lenin and Walt Disney on cryogenics
[--- Sponsors
This year's event is proudly sponsored by: Vault-Tec who will be showcasing their amazing new shelters, and Tesla Motors and SpaceX who will be presenting the latest in self-destructing vehicles.
Special thanks to the law enforcement agencies from many countries for their relentless interest in our activities. We love you guys! #BlueLivesMatter
Do zobaczenia w Krakowie!



0x74686520656E64206973206E696768
[EOF]